So deploying a VPN will as a result hide your real geographical address. Exactly what this is will depend on your.
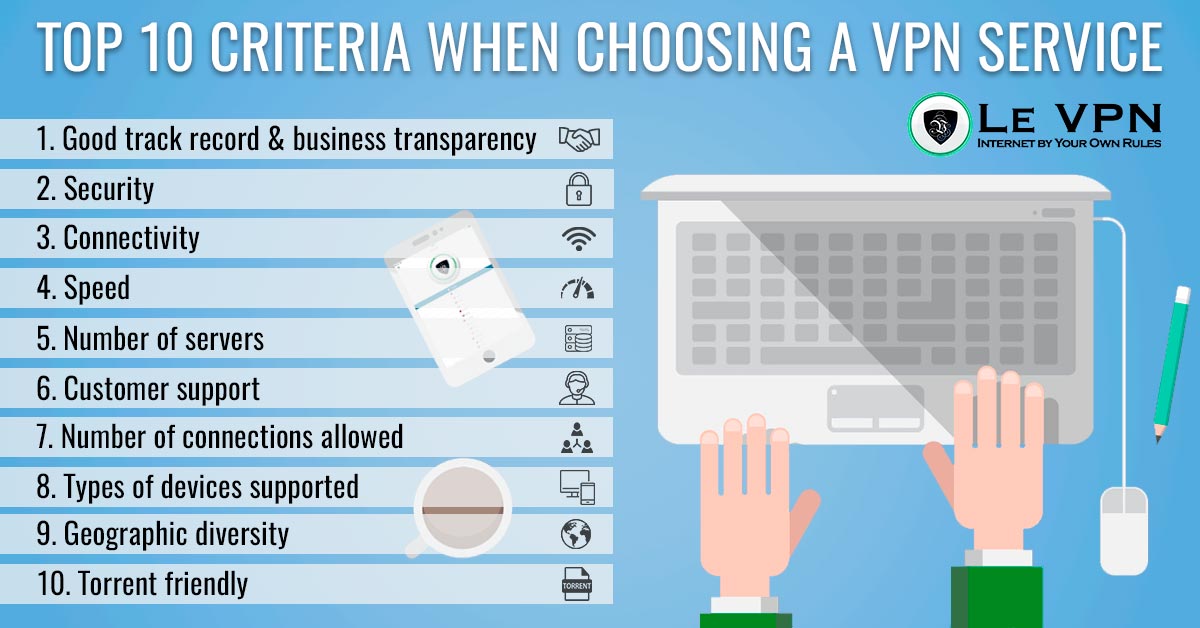
Top 10 Criteria To Pick The Best Vpn Service Le Vpn
For two endpoints to establish an IPSec connection and for traffic to flow through the tunnel successfully the settings on both ends must match 100 percent.

. Before discussing various types of remote VPN connections it is prudent to be aware of remote networking best practices. Some OSs support VPNs natively however usually not the OpenVPN protocol which is best. A virtual private network VPN is defined as a computer network that provides online privacy by creating an encrypted connection on the Internet.
If you have searched a question and bumped into our website just know you are in the right place to get help in your coursework. The Best VPN Providers for Streaming Anonymity Security. And while reading the following paragraphs keep in mind that as bad as what I describe may sound things may be even much worse in many other countries One example is recently introduced legislation to basically do a house search online on your PC or smartphone by hacking your device possibly using.
Marcin will share his best practices for implementing cryptographic VPN as well as advise those customers who are looking. Never use a 1024 bit key for key exchange. Ad We Curated the 7 Best VPN Services.
Describe best practices for using a VPN. Give Conditional Access to resources based on device identity assurance network location and more. We are a professional custom writing website.
5 IPSEC VPN BEST PRACTICES IPSec VPN configuration. After analyzing several VPNs and conducting tests we came up with a shortlist of the eight best VPNs for iPhones below. L2TPIPSEC is still considered secure but OpenVPN is preferable protocol.
Today if you do not want to disappoint Check price before the Price Up. The following sections describe 10 examples of how to use the resource and its parameters. Briefly describe the seven best practices rules for firewall use.
The Not-So-Good VPN Security Risks Third-party VPNs cant create or enforce policies that protect credentials Third-party vendors may sometimes follow a number of VPN practices that are not optimal yet are beyond your control practices that create opportunities for hackers to enter your network. Use the strongest possible authentication method for VPN access. For encryption use AES128 faster or AES256 more secure.
Do you handle any type of coursework. 1 All traffic from the trusted network is allowed out. This allows the users to send the information and access services when they are needed without being stopped by the firewall outbound traffic filter.
The next section provides recommended settings. Get Easy Access to Great Content With Unlimited Bandwidth. Using Vpn To Bet On Sports See Price 2021 Ads Deals and Sales.
Use at minimum 2048 bit key. Thus letting you access various platforms without restrictions. When youre not using a VPN any website you visit can see your real IP address.
Make sure that your network security policy is part of the official company manual and that all the employees are given proper overview of the security policy and training for VPN use. Otherwise the performance of the connection is affected. When following the best practices to secure a VPN its important to also understand the associated challenges.
Best Practices for The Other Azure Network Resources. An organization using VPN should have both antivirus and firewall protection on all company hardware. What must a VPN that proposes to offer a secure and reliable.
The way a VPN works is it hides your real IP address. Indeed there is no point hiding the fact that moving to. We have posted over our previous orders to display our experience.
Compare Now and Find Your Ideal VPN. Example Usage from GitHub. Ad Top 8 VPN Services of 2022 Compared.
Azure AD Conditional Access lets you apply the right access controls by implementing automated access control decisions based on the required conditions. The purpose of this chapter is to describe the best practices for performing such migrations and ultimately to ease the migration process itself. Sharing credentials with co-workers or reusing.
Never use PPTP for VPN it is insecure and broken. This article explains what VPN is and how it works along with its components types functions and best practices for 2021. The VPN Gateway in Network can be configured in Terraform with the resource name azurerm_point_to_site_vpn_gateway.
Welcome to the Cisco Support Community Ask the Expert conversation. Split tunneling is the capability of a remote router or endpoint to connect to more than one network service. Best Practices VPN Routing.
Using a VPN is one of the best ways to keep your iPhone secure. Find the Best VPN for you. Put a security policy in place.
If you dont want to spend money on a VPN there are a few great free VPNs for iPhones. Ad Our Top 10 Best VPN Picks for 2022. Choose The Perfect One For You.
Best practices are. Here are 10 tips to help secure your network while ensuring the benefits of your VPN. Using Vpn To Bet On Sports BY Using Vpn To Bet On Sports in Articles Right.
Furthermore the organization should employ a security as a service or detection monitoring to identify and stop malicious attack on the network before damage occurs. This is an opportunity to learn and ask questions about implementing cryptographic VPN and how to prepare it for the future with expert Marcin Latosiewicz. Network administrators are often reluctant to change firewall vendors due to the perception that the migration process is difficult.

What Is A Vpn Used For 15 Cool Exciting Ways How To Use A Vpn

How To Choose The Best Vpn In 2022 8 Tips For Vpn Beginners

Hola Vpn Free Proxy Vpn For Seo S For Unblocking A Website Or Content In 2021 Competitor Analysis Best Vpn Hola Vpn
0 Comments